
PDF) Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases

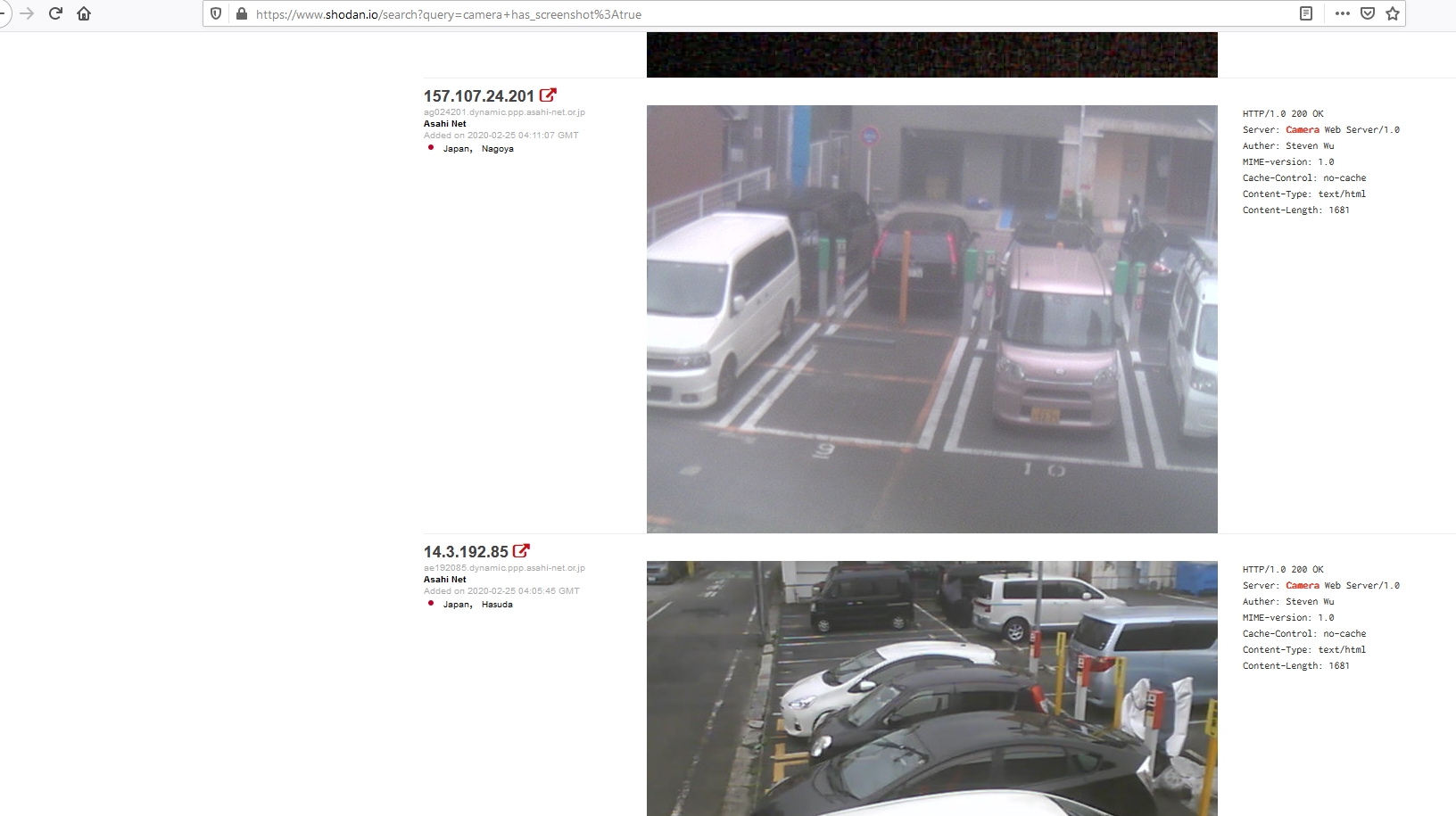
PenTest Edition: Using Shodan to Locate Internet-Connected Devices (Webcams, Servers, Routers, and More) – The Cybersecurity Man
Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
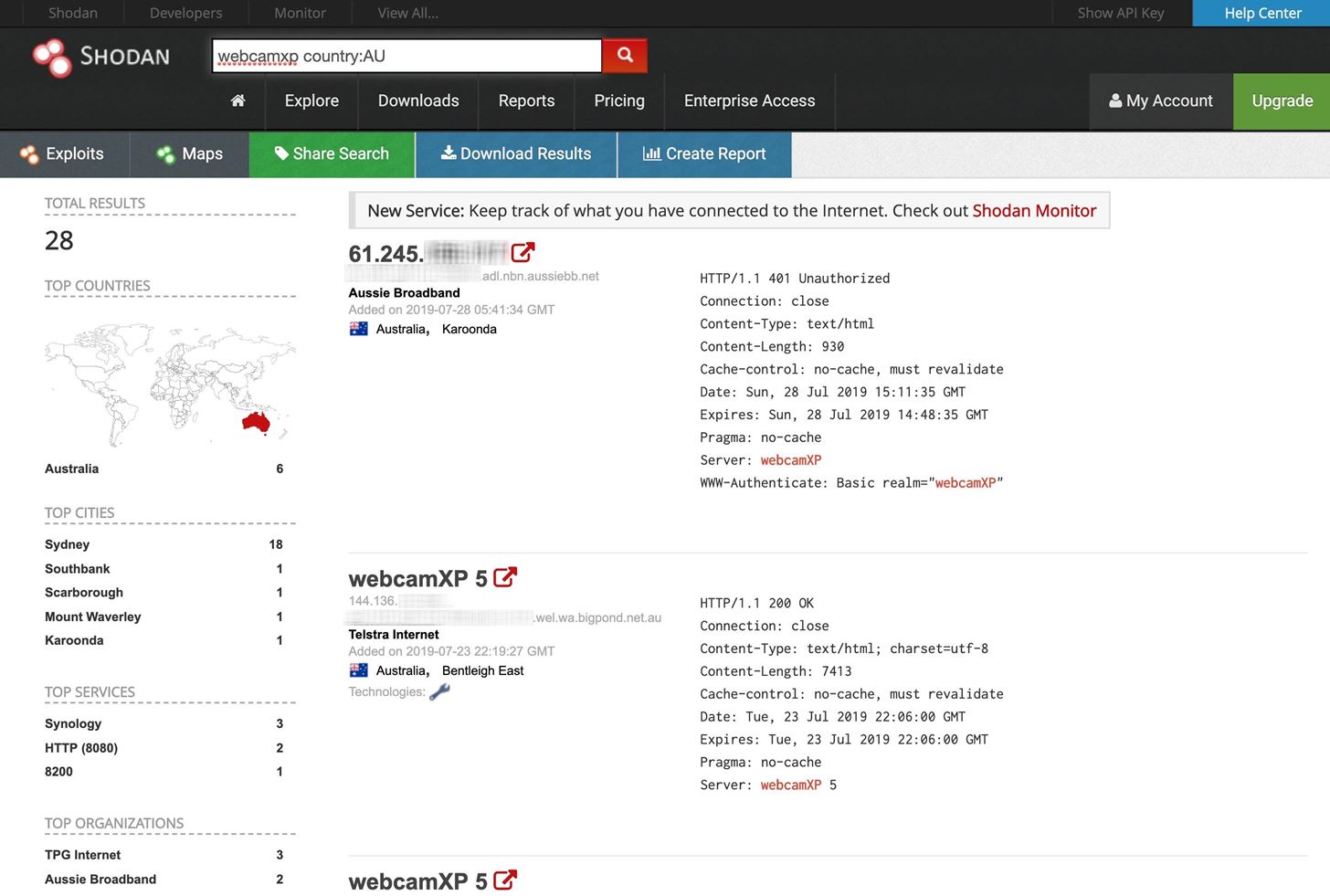
GitHub - jakejarvis/awesome-shodan-queries: 🔍 A collection of interesting, funny, and depressing search queries to plug into shodan.io 👩💻
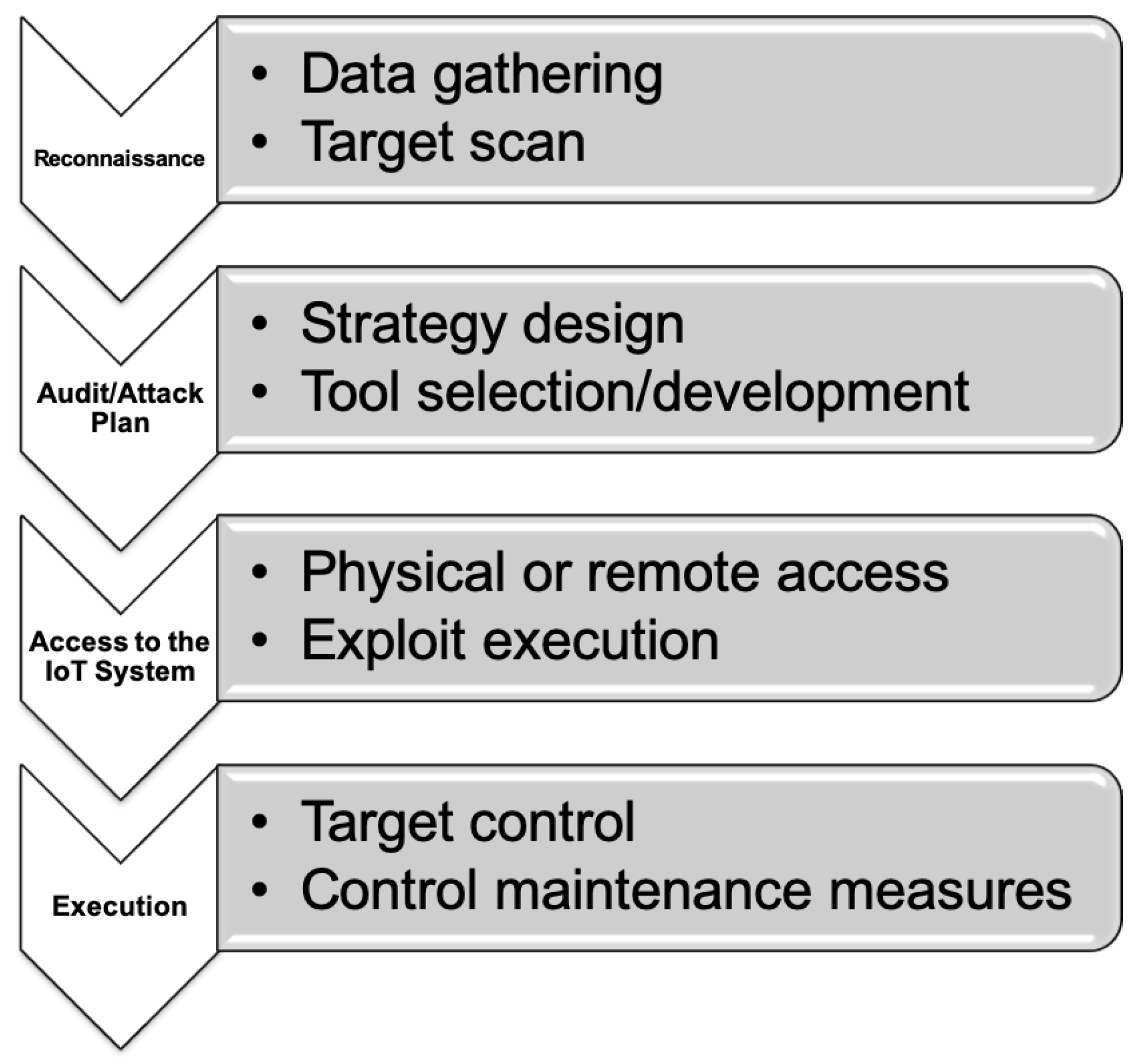
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
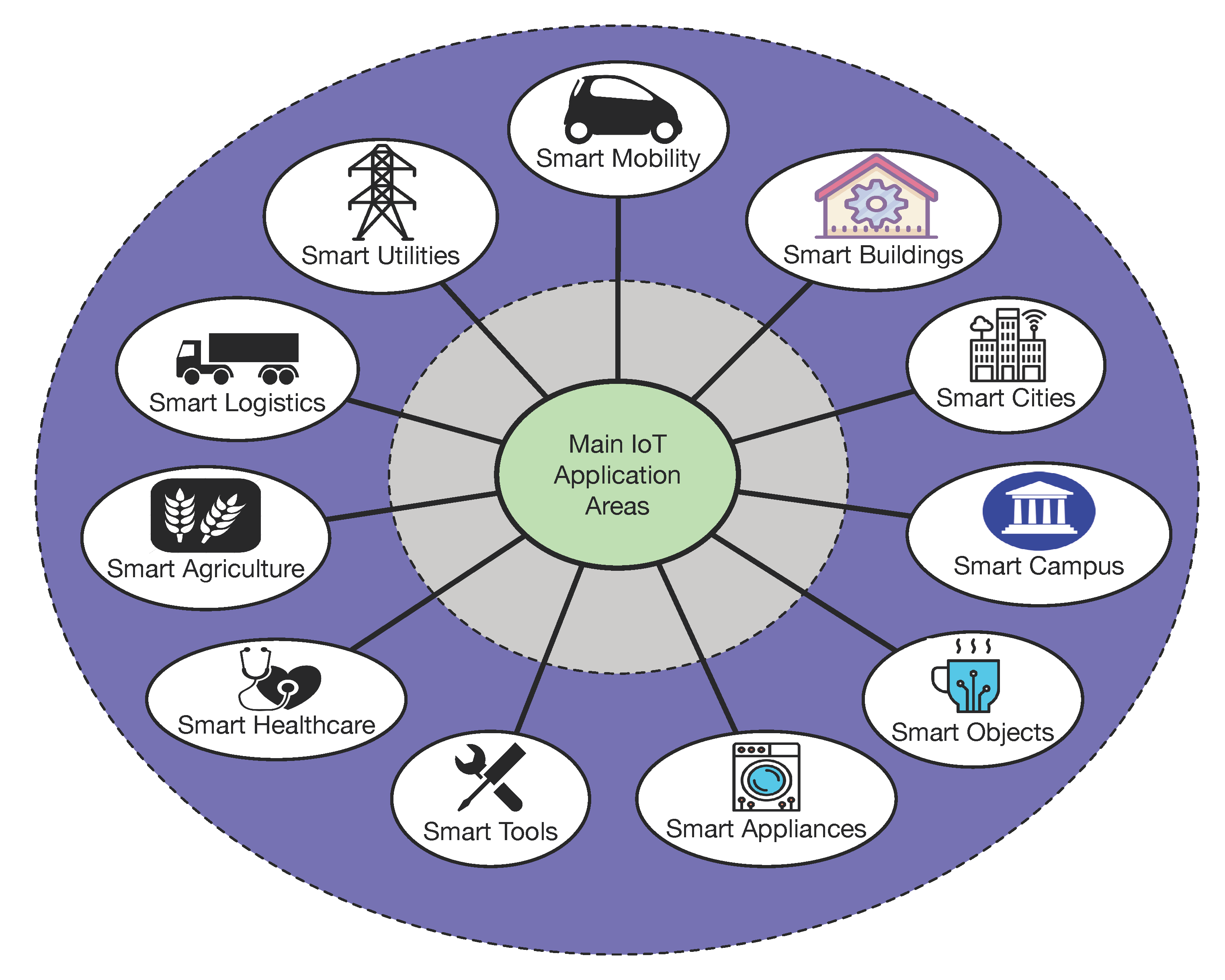
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
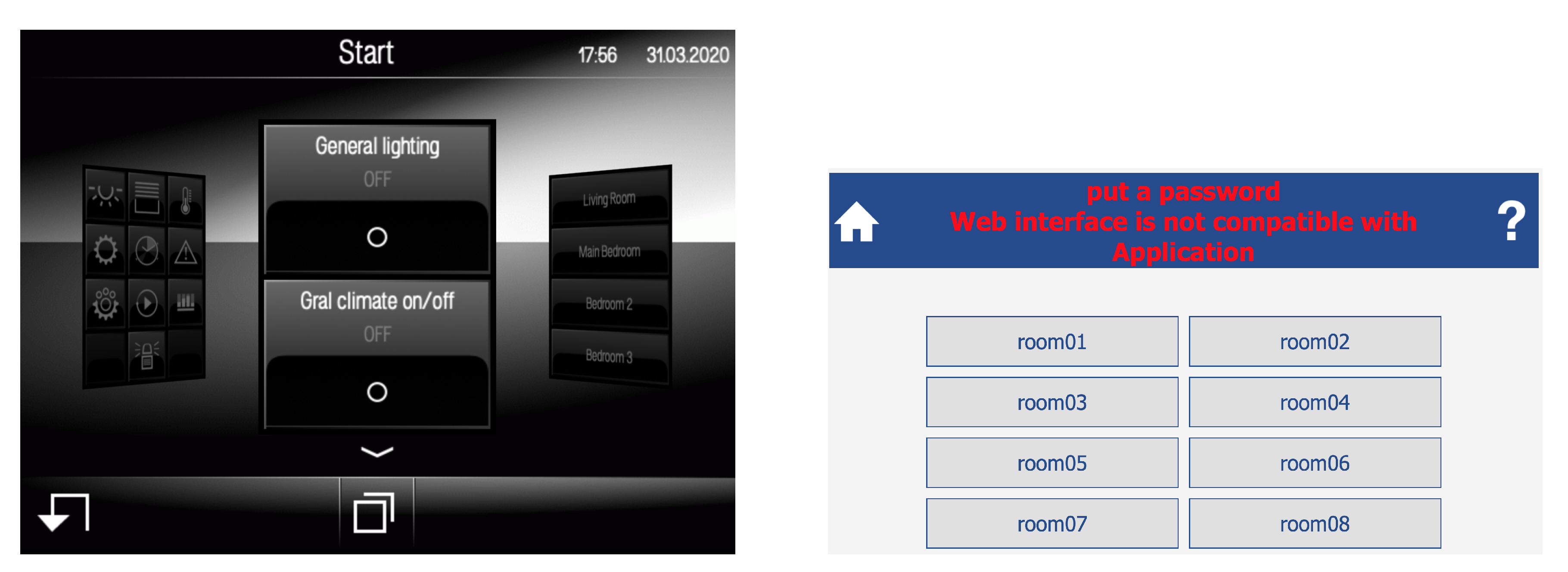
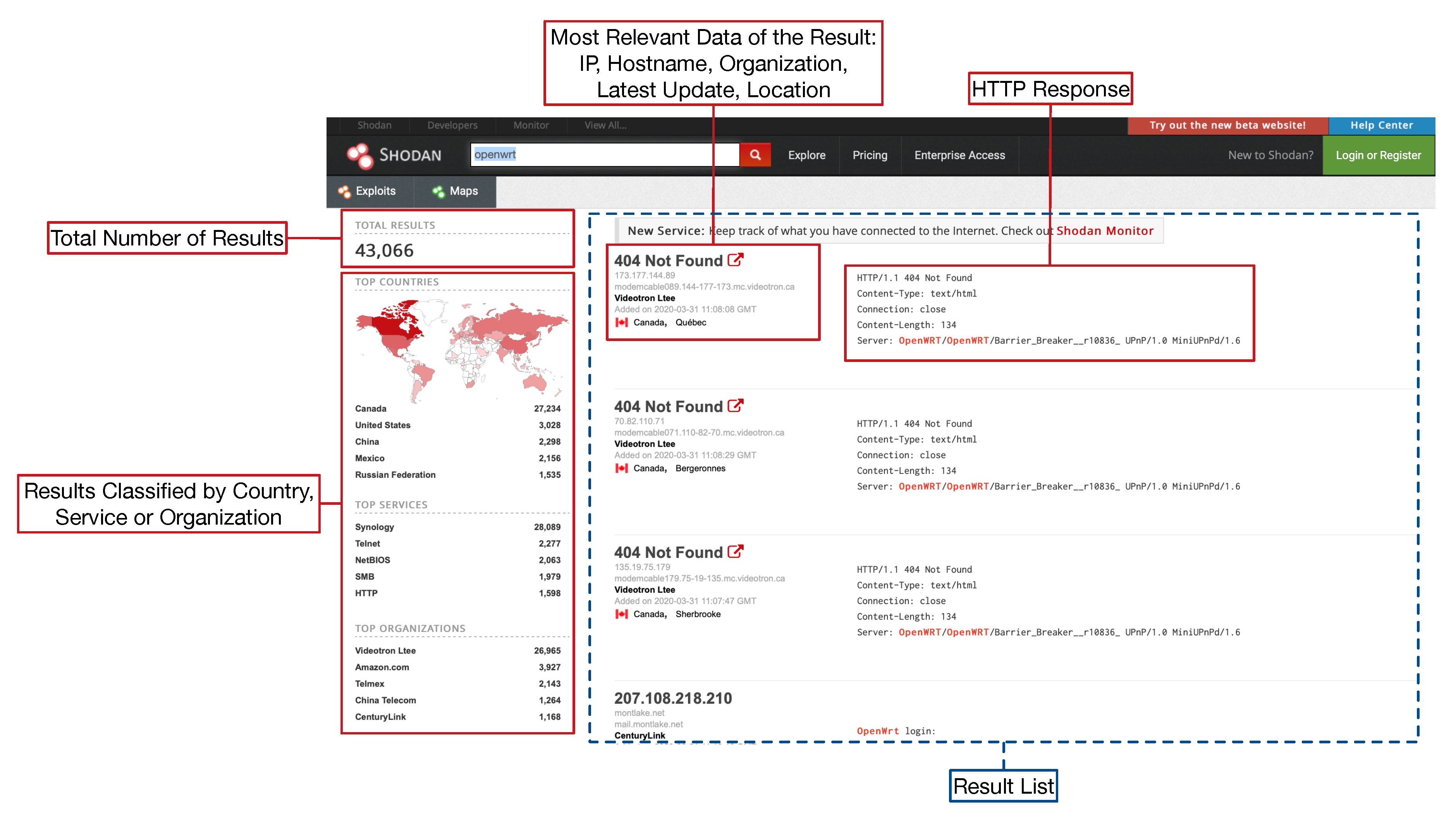
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
![Find Vulnerable Webcams with Shodan [Metasploit Framework] - Yeah Hub Find Vulnerable Webcams with Shodan [Metasploit Framework] - Yeah Hub](https://www.yeahhub.com/wp-content/uploads/2018/06/1.png)



![What Is Shodan? How to Use It & How to Stay Protected [2023] What Is Shodan? How to Use It & How to Stay Protected [2023]](https://www.safetydetectives.com/wp-content/uploads/2021/04/what-is-shodan-3.png)



